The tech industry is an ever-evolving beast, where innovation is the currency and security is the queen guarding the castle. In the kingdom of cyberspace, tech giants wield their power not only by producing dazzling features and devices but by prioritizing the safety of their loyal subjects—us, the users. With great technology, however, comes great responsibility, and our industry bigwigs are ramping up efforts to shield us from the internet’s darker corners. Let’s dive into the most recent strategic moves by Meta and Apple to fend off online predators and thieves alike.
The Digital Age’s Armor: Meta’s New Safeguards for Minors
 Meta has recognized the urgency to protect its younger users across Instagram and Facebook Messenger with a vigilance reminiscent of a medieval knight defending their fortress. While the tech titan had previously clamped down on adults DMing minors, these new measures are akin to the drawing up of a digital-age drawbridge, cutting off message routes for non-followers across the age spectrum. It’s a bold step that reinforces Meta’s commitment to slaying the dragon of online vulnerability for the younger generation.
Meta has recognized the urgency to protect its younger users across Instagram and Facebook Messenger with a vigilance reminiscent of a medieval knight defending their fortress. While the tech titan had previously clamped down on adults DMing minors, these new measures are akin to the drawing up of a digital-age drawbridge, cutting off message routes for non-followers across the age spectrum. It’s a bold step that reinforces Meta’s commitment to slaying the dragon of online vulnerability for the younger generation.
Parental Powers: The Supervisory Magic Wand
 We’re witnessing an enchanting twist in the narrative of digital parenting. The modern-day wielders of family safety, the parents, now have a potent weapon in the form of expanded Instagram supervision tools. These spells allow parents to approve or banish their offspring’s privacy and safety settings changes with a flick of the digital wand. Say goodbye to teens toggling their profiles from private to public on a whim – parental permissions are the new guardianship spell in this enchanted online world.
We’re witnessing an enchanting twist in the narrative of digital parenting. The modern-day wielders of family safety, the parents, now have a potent weapon in the form of expanded Instagram supervision tools. These spells allow parents to approve or banish their offspring’s privacy and safety settings changes with a flick of the digital wand. Say goodbye to teens toggling their profiles from private to public on a whim – parental permissions are the new guardianship spell in this enchanted online world.
Apples Stolen Device Protection: A Modern-Day Cloak of Invisibility for iPhones
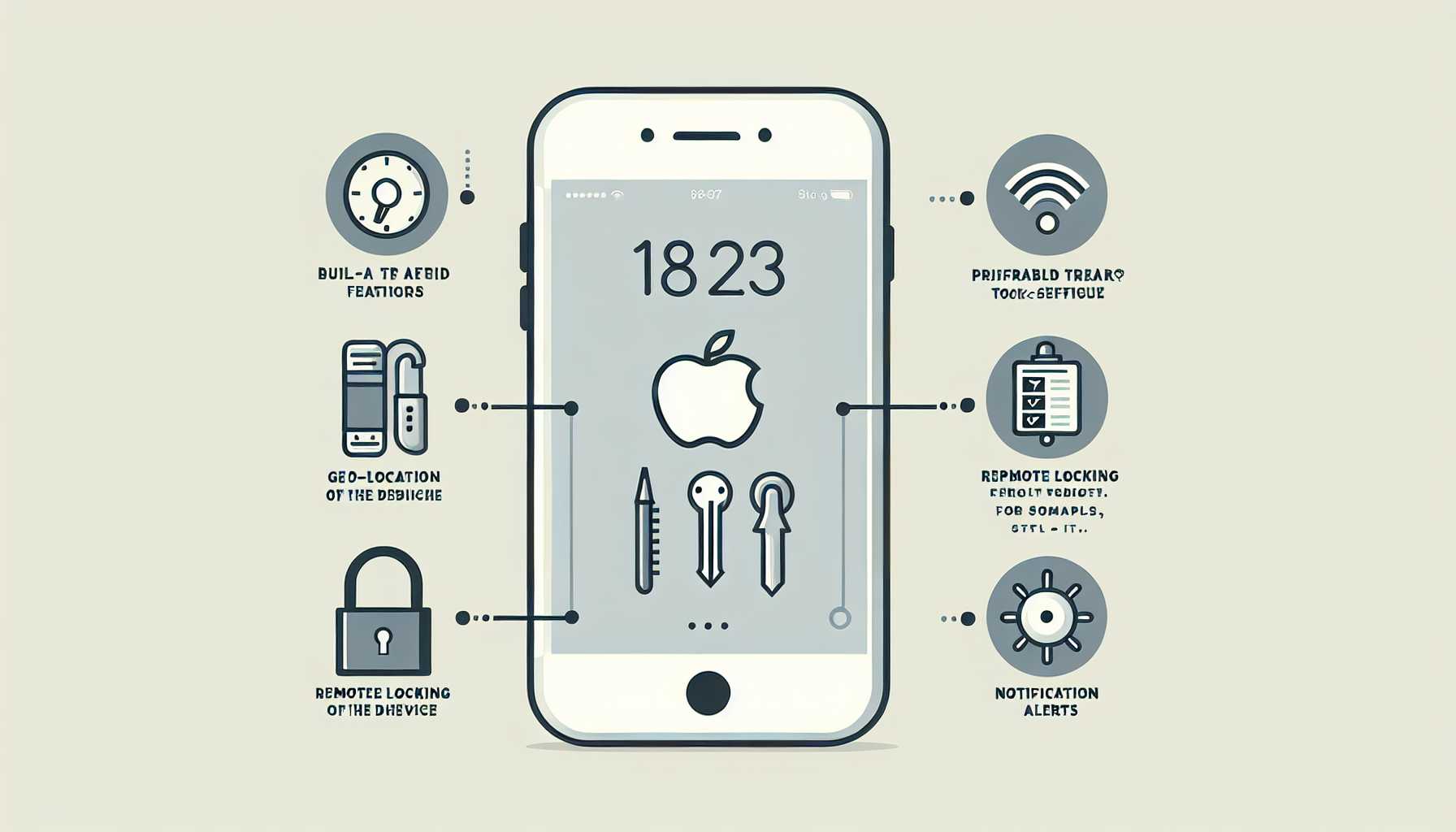 Leaping from the scrolls of fantasy, Apple introduces a digital version of a protection charm with its Stolen Device Protection feature. Imagine a cloak of invisibility for your personal data on the iPhone that thwarts tech-savvy thieves! Once the realm of fiction, this security measure is now very much a part of our Muggle world, where biometrics serve as our incantations to guard against unauthorized data pilfering. With a nod to crime reports and the chaos of having an iPhone snatched, Apple has crafted a powerful protective spell in iOS 17.3.
Leaping from the scrolls of fantasy, Apple introduces a digital version of a protection charm with its Stolen Device Protection feature. Imagine a cloak of invisibility for your personal data on the iPhone that thwarts tech-savvy thieves! Once the realm of fiction, this security measure is now very much a part of our Muggle world, where biometrics serve as our incantations to guard against unauthorized data pilfering. With a nod to crime reports and the chaos of having an iPhone snatched, Apple has crafted a powerful protective spell in iOS 17.3.
The Loose Threads: Is the Privacy Fabric Fraying?
 Not all is well in the tapestry of tech, however. Seemingly, some crafty apps, including familiar names like Facebook and TikTok, appear to be unpicking the very stitches of Apple’s finely woven privacy fabric—collecting user data through cleverly (and sneakily) disguised mechanisms like push notifications. In the shadows of this fleece, they have found ways to clandestinely collect device information, bypassing the user’s intent to shield activities from analytics and ad-trackers. Privacy is our digital right, and any threat to it must be met head-on.
Not all is well in the tapestry of tech, however. Seemingly, some crafty apps, including familiar names like Facebook and TikTok, appear to be unpicking the very stitches of Apple’s finely woven privacy fabric—collecting user data through cleverly (and sneakily) disguised mechanisms like push notifications. In the shadows of this fleece, they have found ways to clandestinely collect device information, bypassing the user’s intent to shield activities from analytics and ad-trackers. Privacy is our digital right, and any threat to it must be met head-on.
The Watchtower’s Warning and the Hope Ahead
 In the watchtower high above the tech landscape, signs of an impending storm are clear. Reports from within Meta’s walls whisper of dangers to child users—an alarming wake-up call to tighten defenses and heighten scrutiny over content and contact protocols. Apple, too, hears the clarion call to action, addressing the detection of data misuse. But there is hope on the horizon; both tech sovereigns are invoking new spells and strengthening their ramparts. As guardians in this digital realm, they must stand firm, adapt, and enhance their protective enchantments. We, the tech community, look to them for stalwart defense and infallible safety. As we march bravely forward, our tech overlords don woven armor of policy and code to shield us from unseen foes. It’s a constant battle where vigilance must be as sharp as the edge of a knight’s blade and as resilient as the stones in a castle wall. Engage with me, dear readers, as we delve further into this tale of tech safeguards and signets of security, where the pen, the code, and policy commands mightier than the sword.
In the watchtower high above the tech landscape, signs of an impending storm are clear. Reports from within Meta’s walls whisper of dangers to child users—an alarming wake-up call to tighten defenses and heighten scrutiny over content and contact protocols. Apple, too, hears the clarion call to action, addressing the detection of data misuse. But there is hope on the horizon; both tech sovereigns are invoking new spells and strengthening their ramparts. As guardians in this digital realm, they must stand firm, adapt, and enhance their protective enchantments. We, the tech community, look to them for stalwart defense and infallible safety. As we march bravely forward, our tech overlords don woven armor of policy and code to shield us from unseen foes. It’s a constant battle where vigilance must be as sharp as the edge of a knight’s blade and as resilient as the stones in a castle wall. Engage with me, dear readers, as we delve further into this tale of tech safeguards and signets of security, where the pen, the code, and policy commands mightier than the sword.





